In this post we will be discussing about the latest Magisk 25.2 update, all the new features and changes that this update brings, from where you can download it, how to install it, and also how to update Magisk to the latest version.
Advertisement
If you have been around the Android rooting and modding scene, chances are that you already know about Magisk, or at least heard of it once.
Magisk was created by topjohnwu (John Wu) as a tool to gain root/superuser access on Android systemless-ly, that is, without touching or altering the /system partition. Over the years, it has phased into a powerful and robust tool that is something way more than just a root solution.
If you’re new to the scene and want to know more about the tool, I suggest you read “The Magisk Story” published by topjohnwu himself.
Advertisement
John, despite working at Google now, has been very dedicated to the project. Thanks to him, we see consistent major updates to Magisk every few months, carrying new features, bug fixes, improvements, and support for new Android versions, all while maximizing compatibility across different OEMs and devices.
With that said, the latest Magisk v25.2 update has been released to the public stable channel. This latest version of Magisk brings re-written magiskinit with improved Sepolicy injection that fixes SELinux compatibility issues, security enhancements for the root management component, fixes several bugs, and more.
Page Contents
What’s new in Magisk v25?
To recap, the previous major Magisk v24 update removed the MagiskHide feature as well as the centralized Magisk modules repo from the app, and introduced Zygisk (Magisk-in-Zygote) and DenyList.
The developer announced the release of Magisk v25.2 update on Twitter. This latest version of Magisk does not bring any user-facing features, but we are seeing some major changes to the integral parts of the core Magisk framework, so let’s take a look at them.
Rewritten Magiskinit with Improved Sepolicy Injection
magiskinit is a binary file that replaces the stock init in the ramdisk of the boot image to inject Magisk services and is the first program to run when your device boots up. The software was initially introduced to support devices that came with system-as-root, but later became a crucial part of Magisk and now supports all devices.
Magisk has been constantly fighting against the increasingly complex partitioning and early mount setups of all kinds of devices, sometimes with weird OEM specific implementations.
— topjohnwu, v25 release notes
These increased difficulties had complicated the magiskinit tool to an extent that maintaining it was not sustainable anymore.
Advertisement
A few months ago, John posted on Twitter about the new sepolicy injection “hack”. After months of working on it, a major portion of Magiskinit has been rewritten from scratch in Magisk v25.
For your reference, the table below demonstrates how the Magisk pre-init boot process worked before, and after its rewrite in the latest update.
| Before | After |
|---|---|
Early mount required partitions. On legacy system-as-root devices, we switch root to system; on 2SI devices, we patch fstab and execute the original init to mount partitions for us. |
Early mount required partitions. On legacy system-as-root devices, we switch root to system; on 2SI devices, we patch the original init to redirect the 2nd stage init file to magiskinit and execute it to mount partitions for us. |
Load sepolicy either from /sepolicy, precompiled sepolicy in vendor, or compile split sepolicy |
Inject magisk services into init.rc |
Patch sepolicy rules and dump to /sepolicy or /sbin/.se or /dev/.se |
On devices using monolithic policy, load sepolicy from /sepolicy; otherwise we hijack nodes in selinuxfs with FIFO, set LD_PRELOAD to hook security_load_policy and assist hijacking on 2SI devices, and start a daemon to wait until init tries to load sepolicy. |
Patch init or libselinux.so to force the system to load the patched policies |
Patch sepolicy rules. If we are using “hijack” method, load patched sepolicy into kernel, unblock init and exit daemon |
Inject magisk services into init.rc |
Execute the original init to continue the boot process |
Execute the original init to continue the boot process |
It’s evident that the new and improved sepolicy injection method is certainly more efficient. It greatly improves SELinux handling by solving several incompatibility issues.
Security Enhancements for MagiskSU
MagiskSU is the key component of the tool that allows you to manage root (superuser) permissions on your device.
With the release of Magisk v25 update, the developer has introduced a few changes to make the root management more secure. To start off, there is a new package tracking system that will prevent malicious UID reuse attacks.
Further, there’s also a new mechanism that verifies the Magisk app’s signature with the distributor’s signature. This should protect the users from unofficial and modded versions of the Magisk app.
Advertisement
For those of you who do not know, the Magisk root daemon grants seamless root access to the Magisk app without any limits. Using a modified version of the Magisk app (even by mistake) can easily introduce a backdoor to your device. This can give malicious actors privileged access to your data and privacy.
So, you should only download and use the original Magisk app provided by the developer through the official source (the project’s Github repository).
Changelogs
Apart from the two major changes mentioned above, there are several other under-the-hood additions, improvements and fixes. For instance, support for Android 13 Generic Kernel Images (GKIs) and Oculus Go has been added, fix for DenyList for apps that use shared UIDs, and more.
Below, you will find the complete changelog of the latest major Magisk v25 update, along with that of the subsequent v25.1 and v25.2 updates as provided by the developer on Github.
Magisk v25.2 Changelog:
- [MagiskInit] Fix a potential issue when stub cpio is used
- [MagiskInit] Fix reboot to recovery when stub cpio is used
- [MagiskInit] Fix sepolicy.rules symlink for rootfs devices
- [General] Better data encryption detection
- [General] Move the whole logging infrastructure into Rus
Magisk v25.1 Changelog:
- [MagiskBoot] Fix ramdisk backup being incorrectly skipped
- [MagiskBoot] Add new feature to detect unsupported dtb and abort during installation
- [Zygisk] Change binary hijack paths
- [App] Fix incorrect recovery mode detection and installation
- [MagiskInit] Fix config not properly exported in legacy SAR devices
- [General] Enforce the Magisk app to always match or be newer than
magiskd
Magisk v25.0 Changelog:
- [MagiskInit] Update 2SI implementation, significantly increase device compatibility (e.g. Sony Xperia devices)
- [MagiskInit] Introduce new
sepolicyinjection mechanism - [MagiskInit] Support Oculus Go
- [MagiskInit] Support Android 13 GKIs (Pixel 6)
- [MagiskBoot] Fix vbmeta extraction implementation
- [App] Fix stub app on older Android versions
- [App] [MagiskSU] Properly support apps using
sharedUserId - [MagiskSU] Fix a possible crash in
magiskd - [MagiskSU] Prune unused UIDs as soon as
system_serverrestarts to prevent UID reuse attacks - [MagiskSU] Verify and enforce the installed Magisk app’s certificate to match the distributor’s signature
- [MagiskSU] [Zygisk] Proper package management and detection
- [Zygisk] Fix function hooking on devices running Android 12 with old kernels
- [Zygisk] Fix Zygisk’s self code unloading implementation
- [DenyList] Fix DenyList on shared UID apps
- [BusyBox] Add workaround for devices running old kernels
Download Magisk v25 from Github
GitHub is the only official home/website/source of Magisk. On several occasions, Magisk’s creator John Wu, as well as XDA-Developers, have advised the users to only download Magisk from GitHub.
For documentation, below is the direct link to download the latest Magisk 25.2 APK from GitHub.
Advertisement
Below are the links for the previous version updates in the v25 release channel:
Note:
Since the release of version 22, core Magisk and the Magisk Manager app have been merged into one single package in .apk file format. This Magisk APK file is also a recovery-flashable package.
TWRP 3.5 and above support flashing of the Magisk APK file just like any other flash-able ZIP file. If you’re using an older or unofficial version of TWRP, simply download the Magisk-v25.2.apk file and change its file extension by renaming it to Magisk-v25.2.zip and flash it through the recovery.
How to Install Magisk v25.2 to Root Android
You can install the latest Magisk v25 on your Android device by using either of the following methods:
- Patching the boot/recovery images: This is the easiest way to install Magisk and is what the developer recommends to use where applicable. It involves patching the boot or recovery image file in the Magisk app and then flashing the resultant patched image to your phone using Fastboot commands.
You can extract the required boot/recovery images from the factory images provided by the OEM, or by dumping the Android OTA Payload. You can also find these images in your device-specific section on XDA-Developers forum or on online repositories such as firmware.mobi. - Flashing through custom recovery: This method involves flashing the Magisk APK/ZIP file through a custom recovery, such as TWRP, OrangeFox, etc. It is generally more suitable for users running a custom ROM.
- Patching the firmware AP tar file: This method is only applicable to Samsung devices launched with Android 9.0 or above. It involves Patching the firmware
APtar file in Magisk app and then flashing the patchedAPtar to your Samsung device using Odin tool.
It is strongly recommended to take a full backup of all your data before you begin installing Magisk (See: Android backup guide). If any issues arise, this backup should help your restore all your data.
The following tutorial will help you install Magisk v25 using the aforementioned methods. I suggest you go through the instructions and familiarize yourself with the procedure before you start performing it.
How to Update to Magisk v25.2
If you already have Magisk installed on your device, you do not need to re-install it. You can easily update to Magisk 25.2 by following the steps listed below.
- Launch the Magisk app on your device.
- Press the settings button (cogwheel) located on the top-right of the app window.
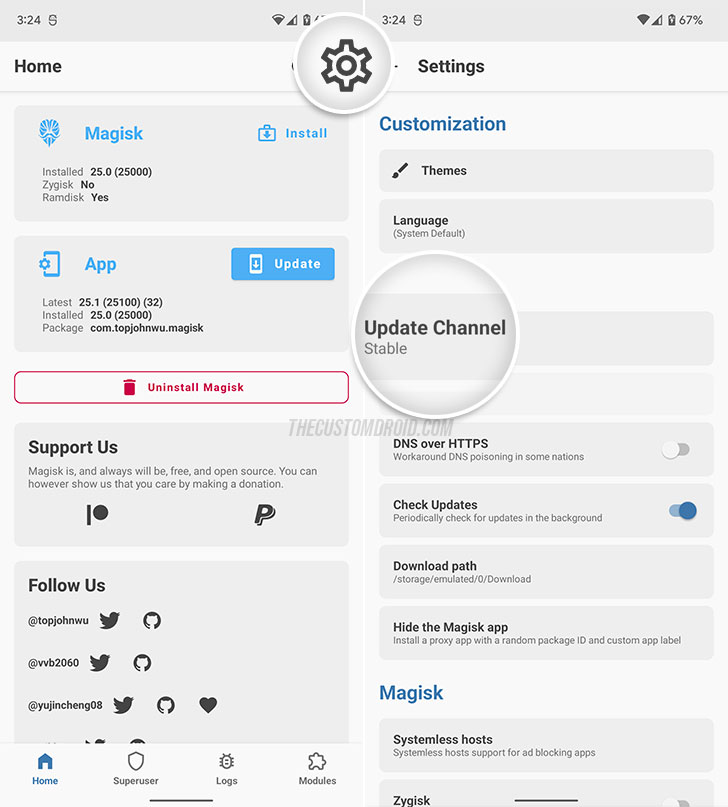
- Tap on “Update Channel” and select “Stable” (if it is not already selected).
- Go back to Magisk app’s main screen.
- Press the refresh icon located on the bar at the top and wait for the app to fetch the latest Magisk update.
- Press the “Update” button on the “App” card and then press “Install”.
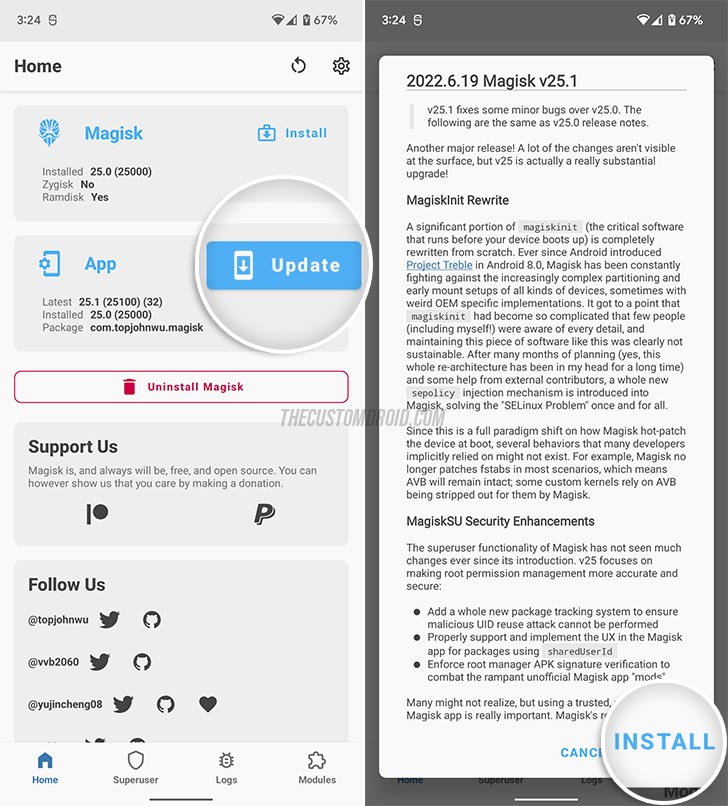
- When prompted, install the latest Magisk app by following the on-screen instructions. The app will automatically relaunch after updating.
- Press the “Update” button on the “Magisk” card.
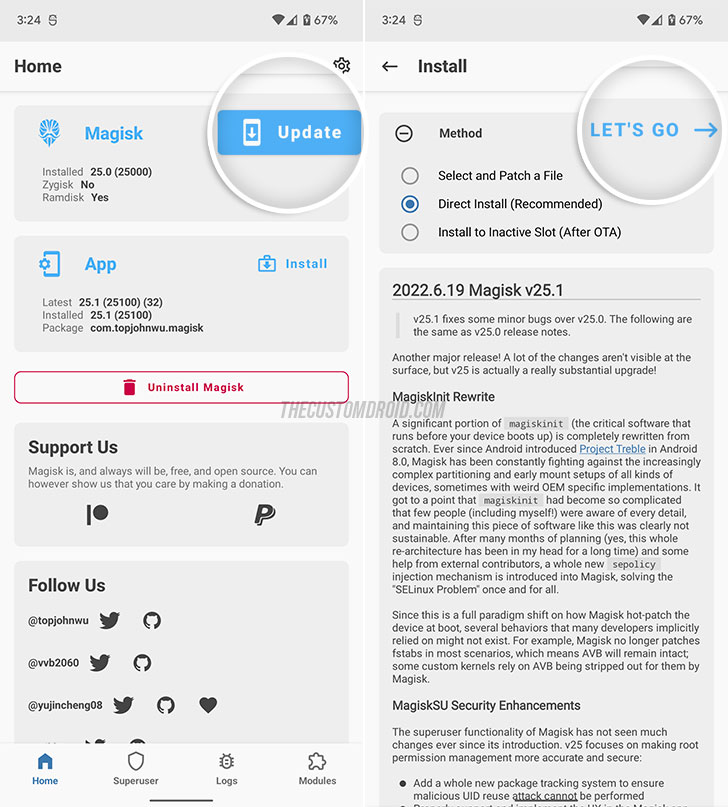
- Select “Direct Install” as the preferred method of installation and press “LET’S GO“.
- Press the “Reboot” button once the installation finishes.
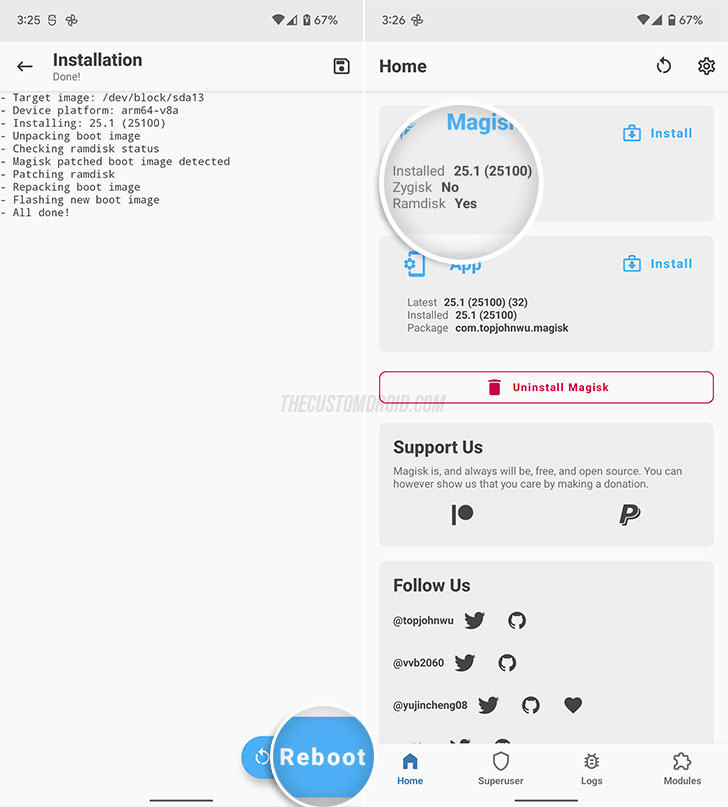
Congratulations! When your device boots, it should have the latest Magisk version installed and you can confirm the same by launching the Magisk app. All your installed modules and settings should remain intact after the update, so you can continue using your device as usual.
What’s next? — After the release of the latest Magisk v25 update, topjohnwu mentioned that he will now experiment by introducing the Rust Programming Language (known to be the most loved programming language) into the project. While this does not mean much for the end-users at the moment, it should be exciting to see what new changes and improvements it brings to the next major version of Magisk. (Update: The Magisk v25.2 update is now live and it moves the whole logging environment into Rust)
If you have any questions about this latest version of Magisk, feel free to ask. If you encounter bugs, you can report them under the Issues section on GitHub. While doing so, try and be as descriptive as possible and provide a logcat so that John can debug the issue quickly and roll out a fix in the next update.
Source: Magisk’s Github